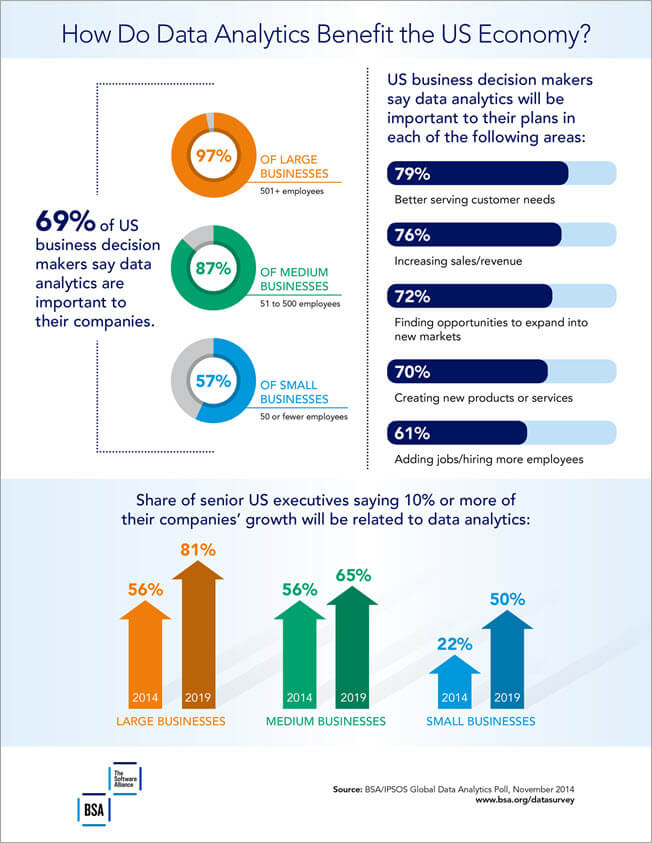
The Cyber Kill Chain consists of 7 steps. Reconnaissance weaponization delivery exploitation installation command and control and finally actions on objectives.
 The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
Step 1 Reconnaissance.

Cyber kill chain steps. The seven steps of the Cyber Kill Chain enhance visibility into an attack and enrich an analysts understanding of an adversarys tactics techniques and procedures. Each stage demonstrates a specific goal along the attackers path. It was developed by Lockheed Martin.
The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data. Ad Explore new cybersecurity trends technologies and approaches. The kill chain helps us understand and combat ransomware security breaches and advanced persistent attacks APTs.
Designing your monitoring and response plan around the cyber kill chain model is an effective method because it focuses on. Each stage of the Cyber Kill Chain is related to a certain type of threat both external and internal. How the Cyber Kill Chain Works in 7 Steps.
What are the 7 steps of the Cyber Kill Chain. According to Bob Hansmann Websenses director of product marketing cyber criminals now provide tailored services for every step of the kill chain and even have aggregators that pull together whole attack campaigns. For the most part whatever threat you face from malware phishing insider threats and more it is likely that they will fall into one or more of the activities on the kill chain.
The model identifies what steps the cyber adversaries must complete in order to achieve their objectives. The cyber kill chain is a traditional security model that describes an old-school scenario an external attacker taking steps to penetrate a network and steal its data breaking down the steps of the attack to help organizations prepare. The 7 Essential Steps of the Cybersecurity Kill-Chain Process.
The cyber kill chain is a sequence of stages required for an attacker to successfully infiltrate a network and exfiltrate data from it. Ad Explore new cybersecurity trends technologies and approaches. Together we can make networks devices and applications more secure.
Its becoming more specialized aligned with the 7 steps in the kill chain. The Cyber Kill Chain is a model that describes and explains various stages of a cyber attack. Together we can make networks devices and applications more secure.
100 Predictable Pricing Guarantee for Managed Services. The idea behind it is to identify itemise and prevent hostile cyber activity such as intrusion of a network.