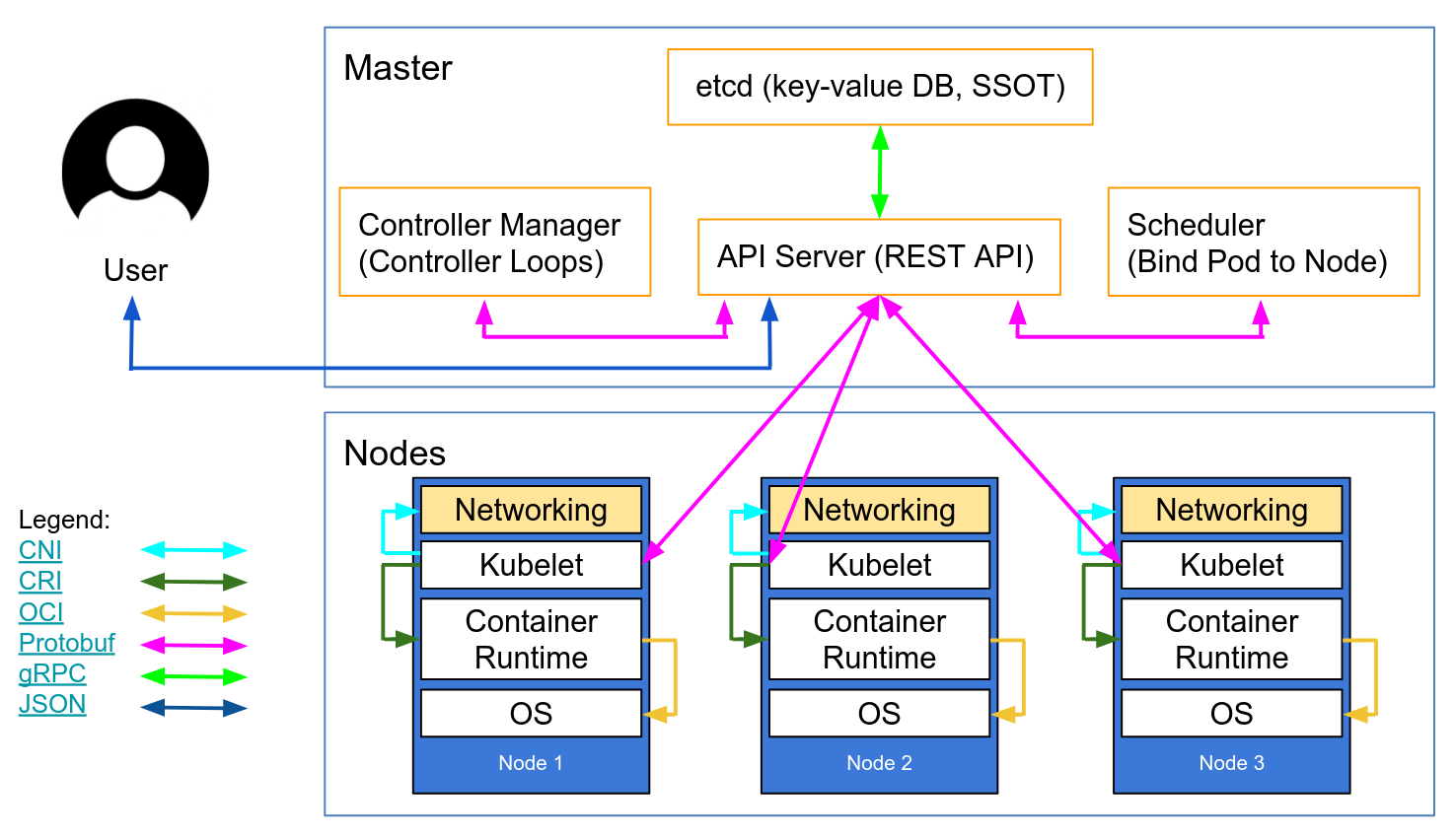
The vulnerability CVE-2018-1002105 enables attackers to compromise clusters via the Kubernetes API server allowing them run. In the following sections well take a deep dive into some Kubernetes security best practices that will help you avoid issues when deploying your own K8s instance.
 11 Ways Not To Get Hacked Kubernetes
11 Ways Not To Get Hacked Kubernetes
During your periodic audits ensure that these practices remain in place and modify configurations as needed.

Kubernetes security best practices. Get Results from 6 Engines at Once. The authors of this guide are running Kubernetes in production and worked on several K8s projects to learn about security flaws the hard way. Last month the Kubernetes ecosystem was shaken by the discovery of the first major security flaw in Kubernetes the worlds most popular container orchestrator.
Kubernetes Security - Best Practice Guide This document acts as a best practice guide to Kubernetes security. Authentication Authorization and Access Control with K8s Namespaces A cluster can be used for distinct environments and purposes. People and Process Are Critical.
Kubernetes sometimes abbreviated as K8s helps you efficiently manage clusters of. Infrastructurecloud administrators can potentially access the nodes storage andor backups which may contain unencrypted data unless the steps in 2 were taken to encrypt data at rest. Best practice guidance One of the most important ways to secure your cluster is to secure access to the Kubernetes API server.
Least privilege must be enforced. K8s is a powerful platform which can be abused in many ways if not configured properly. 9 Kubernetes security best practices everyone must follow.
People and Process Are Critical. Using this type of model to prevent widespread access enables better containment of. It is the best way to manage or orchestrate large clusters of containers at scale.
Ad Search Kubernetes Best Practices. Although their recommendations are a. Kubernetes Security During Build Scan your image and source code As with any application implementing application security testing best practices of using various scanning tools such as SAST DAST IAST or SCA will help ensure your code is as secure as.
While this is far from an exhaustive list here are some best practices for Kubernetes security at various stages to get you started. Integrating security automation levers at key points throughout the full pipeline can help to ensure that Kubernetes deployments can be created and updated safely and that application development can proceed at a suitable pace while any vulnerabilities or signs or unauthorized behaviors are swiftly detected. They also have specific benchmarks for EKS GKE and OKE from Oracle Cloud.
Kubernetes Security Best Practices Julie Peterson December 3 2020 Application Security Kubernetes is an open source orchestration platform for containerized workflows. Here are some important tips on best Kubernetes deployment practices. Ad Search Kubernetes Best Practices.
These three tips will help to ensure Kubernetes security. Check out the CIS Kubernetes Benchmark document for more security best practices. To control access to the API server integrate Kubernetes RBAC with Azure Active Directory Azure AD.
Enable role-based access controls RBACs. The CNCF recently released 9 Kubernetes Security Best Practices Everyone Must Follow in which they outline nine basic actions that they recommend people take with their Kubernetes clusters. Kubernetes Security Best Practices When configuring and verifying your Kubernetes security there are several best practices you should apply.
The best practices we highlight here are aligned to the container lifecycle. Getting Started with Kubernetes Security. With so many Kubernetes security considerations it can be difficult to know how to get started and stay secure.
Use a Supported Kubernetes Distribution Service. Build ship and run and are specifically tailored to Kubernetes deployments. But also be aware of their security defaults.
Configuring them requires intimate knowledge with Kubernetes and the deployments security requirements. They usually have better defaults for your security posture and the costs for maintaining the control plane can be extremely low. By default Kubernetes administrators can access all Secrets stored within the cluster.
Get Results from 6 Engines at Once.