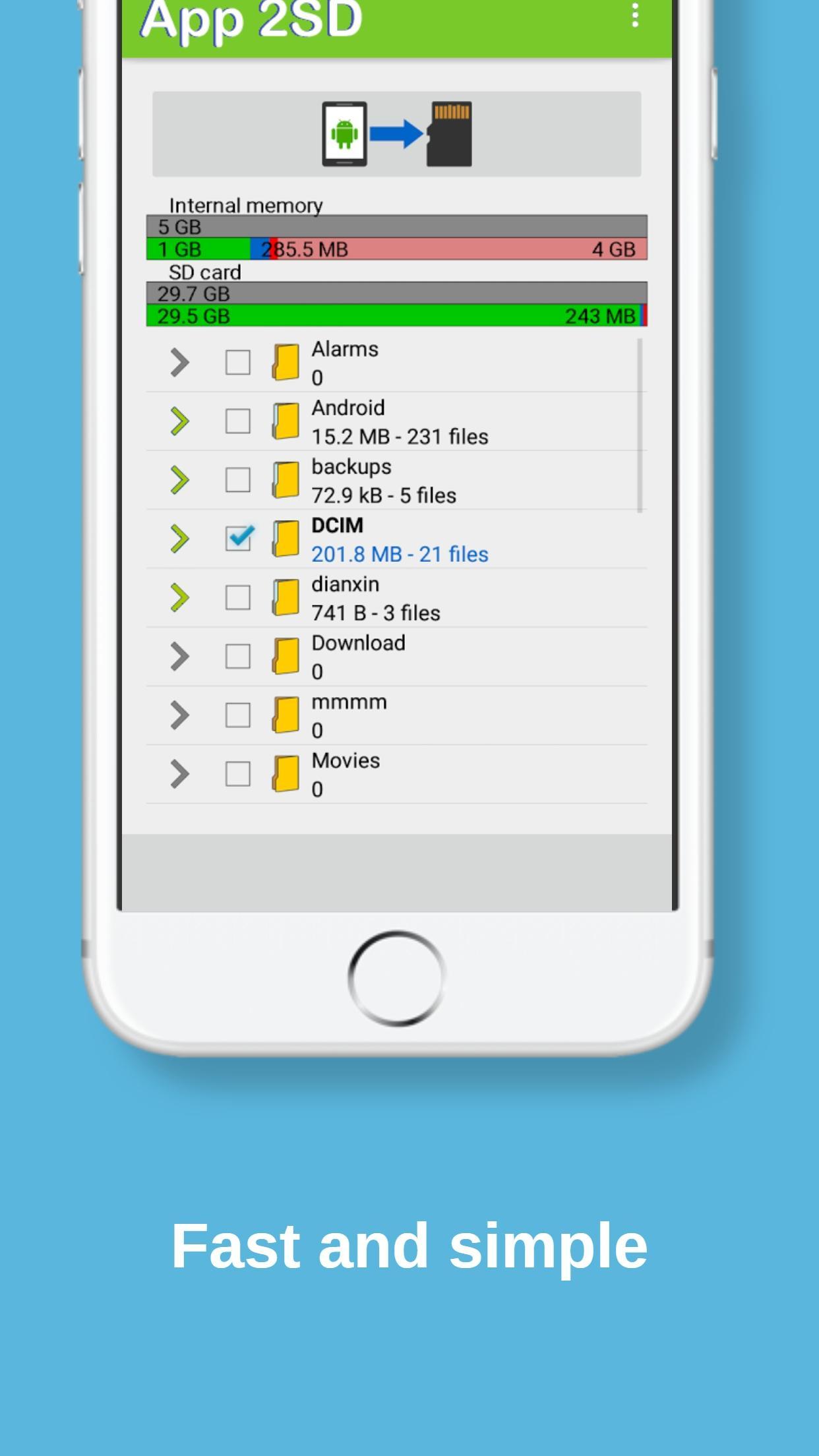
This testing approach focuses on the input that goes into the software and the output that is produced. Black box testing is used to test the system against external factors responsible for software failures.
A black box refers to a system whose behavior has to be observed entirely by inputs and outputs.

Black box system. A device system or object which can be viewed solely in terms of its input output and transfer characteristics without any knowledge of its internal workings that is its implementation is opaque black. Consider the mass-spring-damper system described in Dynamic Systems and Models. Ad our team can help with anything from a minor reorganisation to a full scale internal move.
Additionally This site is NOT endorsed by Facebook in any way. A black box in a general sense is an impenetrable system. Better ways of doing things.
The algorithm takes millions of data points as inputs and correlates specific data features to produce an output. Introduction to black box systems where you cant know whats going on in the inside you can only control the inputs and observe the corresponding outputs. The FLYHT Aerospace equipment has even been installed on 400 aircraft.
First Air Canada is the only airline that uses the FLYHT system. The black box is a powerful technique to check the application under test from the users perspective. By implication black box models are lumped together with parameter models.
That process is largely self-directed and is generally difficult for data scientists programmers and users to interpret. A black box is a function representing a set of concert system into which stimuli S impinge and out of which reaction R emerges 11. One of them FLYHT Aerospace Solutions based in Canada.
They provide a black box streaming service. Domestic International Packers and Movers Service In London. Black box models are simply the functional relationships between system inputs and system outputs.
Click Here To Watch The Free Webinar Now. Te constitution and structure of. If the black boxes truly appeared from the very first time that you powered on your new PC you really should bring that to the manufacturers attention.
The boxes do not appear to be icons given their shape and the fact that one of them is overlapping your Malwarebytes icon. In science computing and engineering a black box is a device system or object which can be viewed in terms of its inputs and outputs without any knowledge of its internal workings. Such a sub-system whose processes are not defined is called a black box system.
Black box is a software testing style that can apply to different test methodologies. The parameters of these functions do not have any physical significance in terms of equivalence to process parameters such as heat or mass transfer coefficients reaction kinetics and so on. The transformation process in certain sub-system especially at the lowest level may not be defined.
A black-box penetration test determines the vulnerabilities in a system that are exploitable from outside the network. Even if the internal structure of the application under examination can be understood the tester chooses to ignore it. Domestic International Packers and Movers Service In London.
In most cases you choose a model structure and estimate the model parameters using a single command. Ad our team can help with anything from a minor reorganisation to a full scale internal move. This site is not a part of the Facebook website or Facebook Inc.
You can use the System Identification app or commands to estimate linear and nonlinear models of various structures. The overall requirement is for less complexity and therefore more transparency in IoT platforms and solutions. However the inputs and outputs are known.
If you do not. Unlike the black box system in general which will record flight data since it was still on the ground. Black box testing is a powerful testing technique because it exercises a system end-to-end.
Deep learning modeling is typically conducted through black box development. Black boxes have the effect of reducing flexibility and increasing costs in a system whose key benefit is driving new efficiencies. Just like end-users dont care how a system is coded or architected and expect to receive an appropriate response to their requests a tester can simulate user activity and see if the system.
Your computer should work properly from Day 1 and you have a warranty. This means that black-box penetration testing relies on dynamic analysis of currently running programs and systems within the target network.