Role-based access control RBAC and attribute-based access control ABAC are two ways of controlling the authentication process and authorizing users. Role Based Access Control RBAC is a critical capability for organizations that deploy applications into the cloud.
 Does This Make Sense As A Way To Implement Role Based Access Control Stack Overflow
Does This Make Sense As A Way To Implement Role Based Access Control Stack Overflow
Azure RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management of Azure resources.

What is role based access control. Role-based access control RBAC is a method of restricting network access based on the roles of individual users within an enterprise. This infers that data consumers can only access data that pertains to their job functions. In the realm of computer systems security Role-Based Access Control RBAC is a process applied to restrict system access to only authorized users.
Role-Based Access Control RBAC is one of the most commonly used methods for controlling access to the different areas of an organizations IT system although it is more popular with larger organizations. Role-based access control RBAC also known as role-based security is an access control method that assigns permissions to end-users based on their role within your organization. Margaret Rouse of TechTarget defines role-based access control as a method of restricting network access based on the roles of individual users within an enterprise.
Role-Based Access Control or what is simply known as RBAC provides the ability to restrict access to certain systems based on the persons role within the organizationThis has become one of the main access controls used for security purposes. Roles basically refer to the level of access the different employees have in the network. Azure role-based access control Azure RBAC helps you manage who has access to Azure resources what they can do with those resources and what areas they have access to.
Controlling user access to applications and resources within the cloud is a necessary step towards maintaining the security of the organizations information assets and proactively protecting against cyber attacks. Role-based access control is a way to provide security because it only allows employees to access information they need to do their jobs while preventing them from accessing additional information that is not relevant to them. Today it is used by the majority of large businesses and enterprise organizations.
Table of contents. Role-Based Access Control RBAC is a security paradigm whereby users are granted access to resources based on their role in the company. Role-based access control RBAC is an approach to data security that permits or restricts system access based on an individuals role within the organization.
Role-based access control RBAC is a method of access security that is based on a persons role within a business. RBAC lets employees have access rights only to the information they need to do their jobs and prevents them from. RBAC provides fine-grained control offering a simple manageable approach to access management that is less error-prone than individually assigning.
RBAC if implemented correctly can be an effective way of enforcing the principle of least privilege. With RBAC users are assigned roles and roles are assigned permissions such as create read update and delete. Role-based access control RBAC is an approach to handling security and permissions in which roles and permissions are assigned within an organizations.
 Role Based Access Control Youtube
Role Based Access Control Youtube
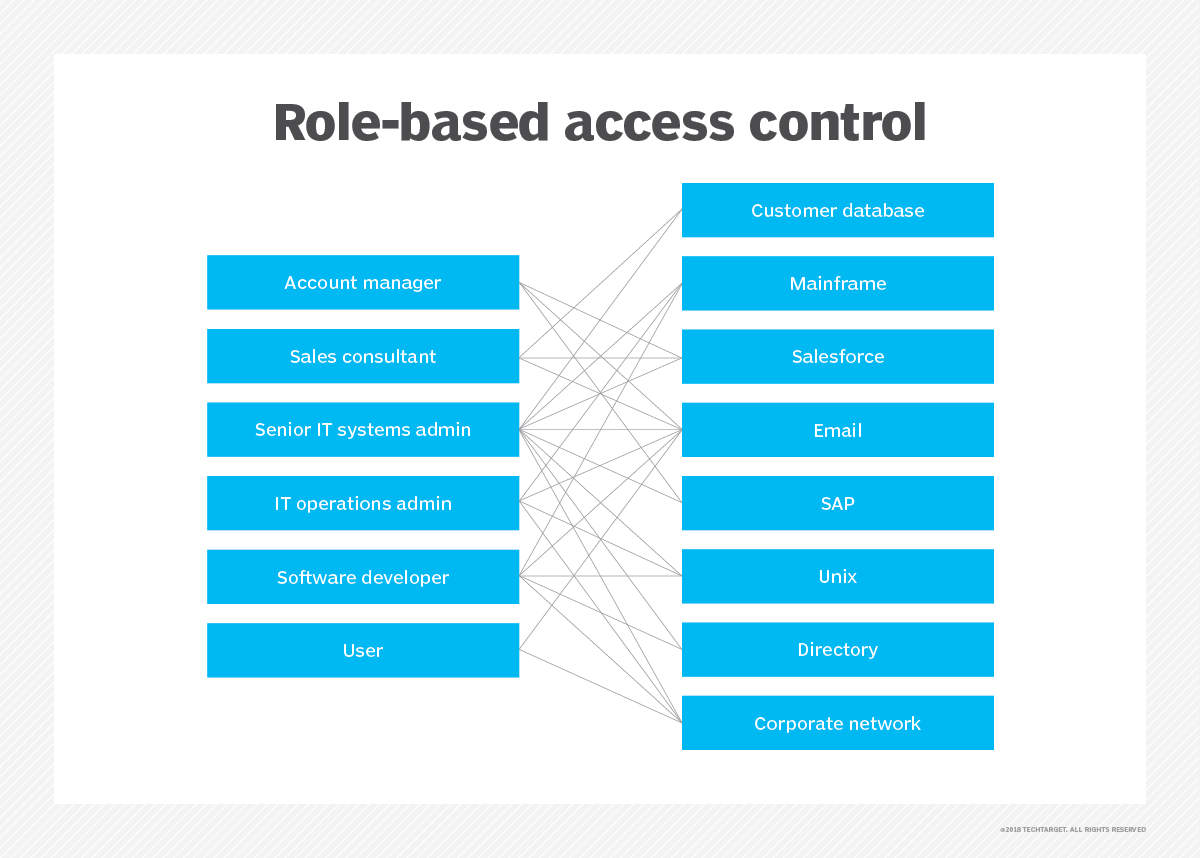 Sample Role Based Access Control In Cloud Alibaba Cloud Developer Forums Cloud Discussion Forums
Sample Role Based Access Control In Cloud Alibaba Cloud Developer Forums Cloud Discussion Forums
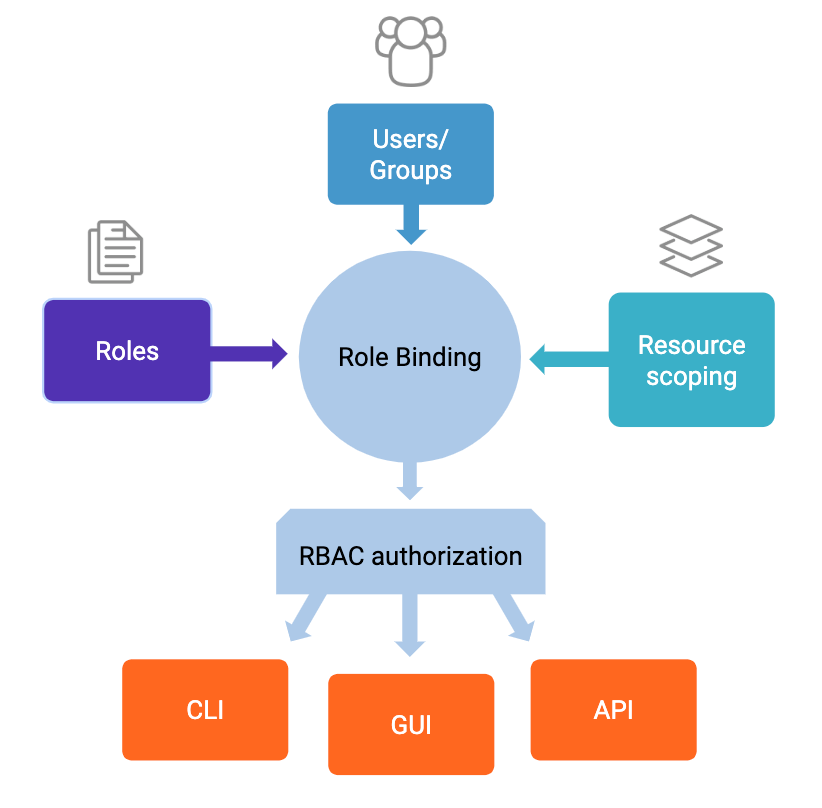 Authorization Using Role Based Access Control Confluent Documentation
Authorization Using Role Based Access Control Confluent Documentation
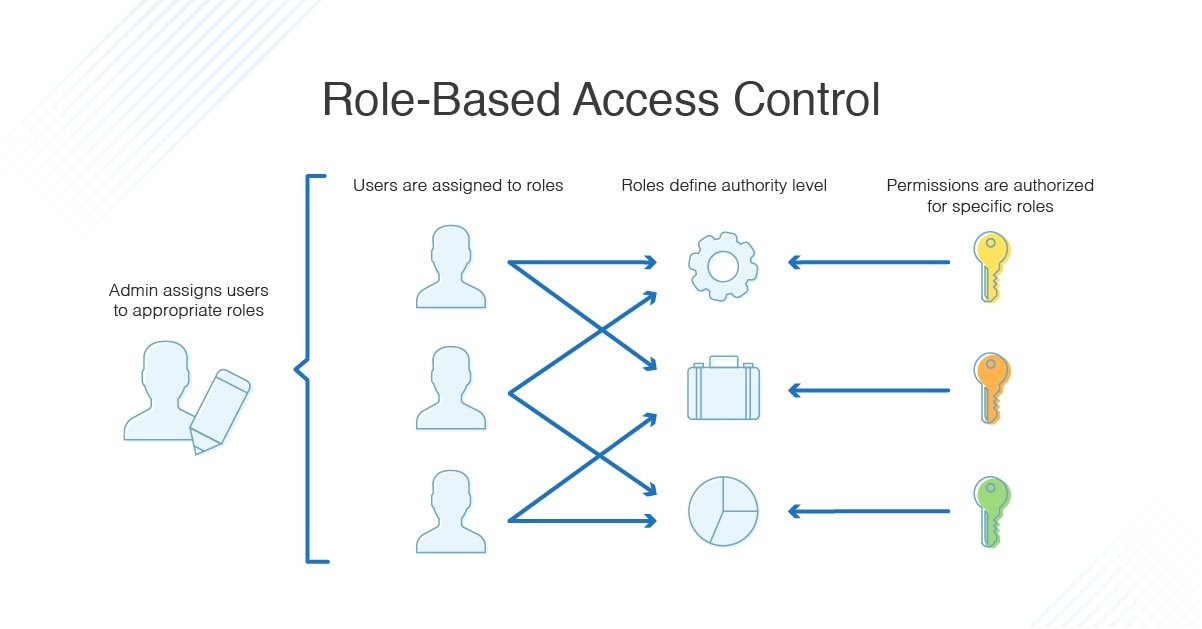 Rbac Vs Abac Access Control What S The Difference Dnsstuff
Rbac Vs Abac Access Control What S The Difference Dnsstuff
 Role Based Access Control Model Download Scientific Diagram
Role Based Access Control Model Download Scientific Diagram
 Rule Based Access Control Nengu
Rule Based Access Control Nengu
 Configure Role Based Access Control Rbac Axway Open Documentation
Configure Role Based Access Control Rbac Axway Open Documentation
 Role Based Access Control Vs Attribute Based Access Control How To Choose Ekran System
Role Based Access Control Vs Attribute Based Access Control How To Choose Ekran System
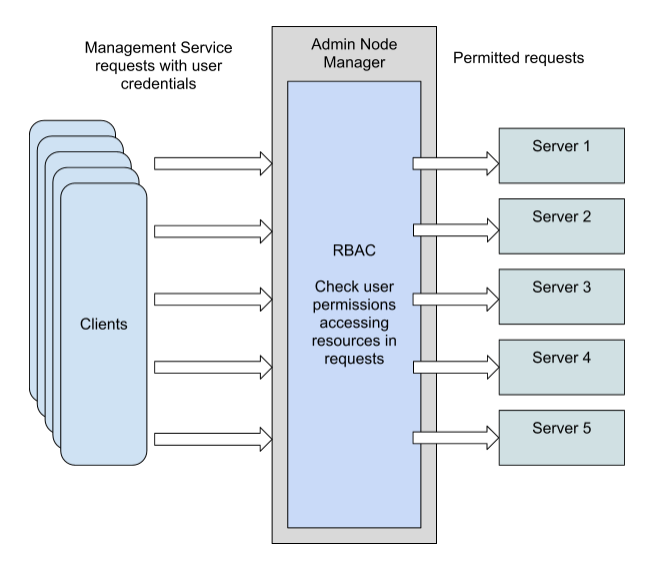 Configure Role Based Access Control Rbac
Configure Role Based Access Control Rbac
 Role Based Access Control Computer Security A Brief Look
Role Based Access Control Computer Security A Brief Look
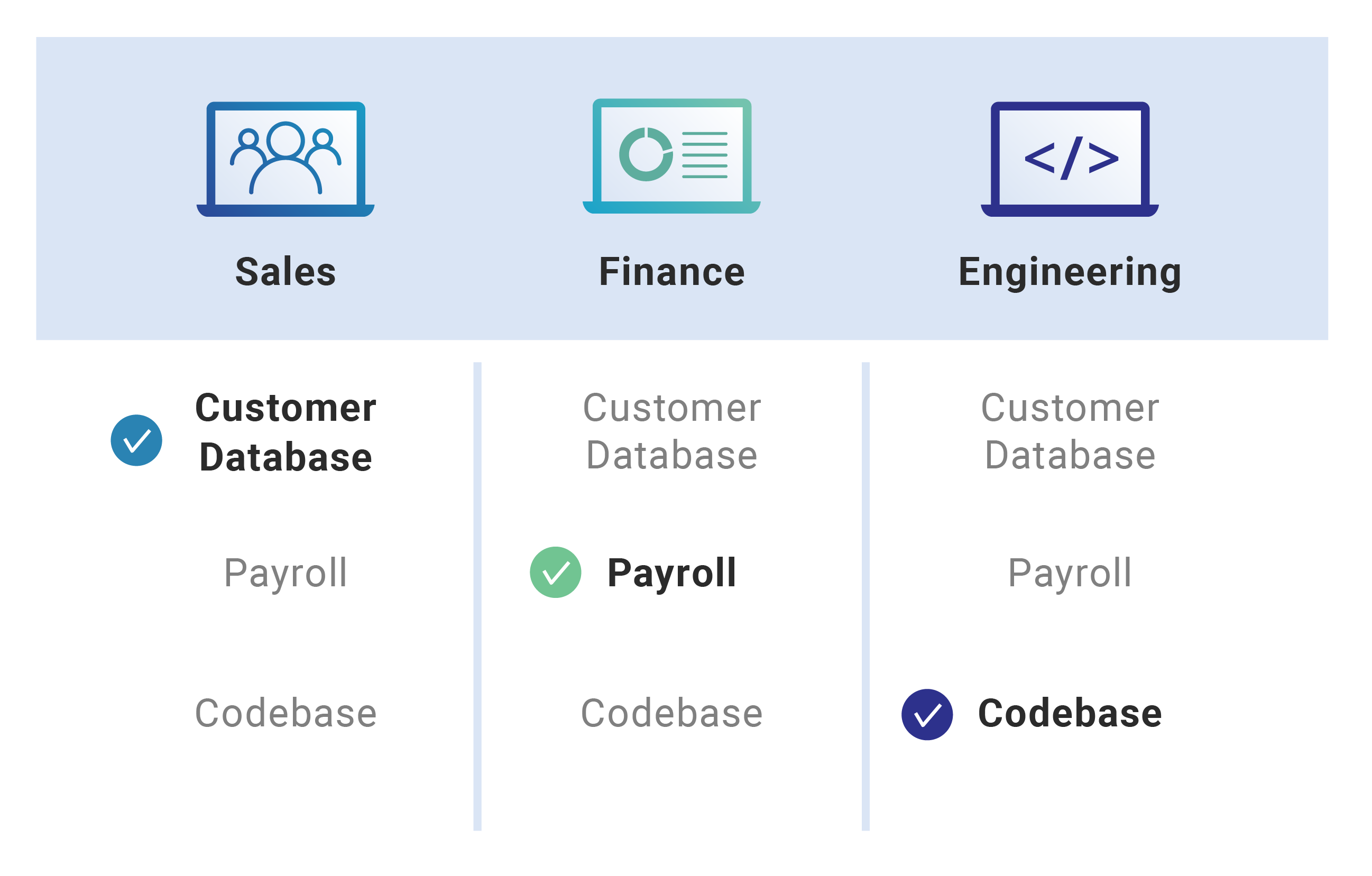 What Is Role Based Access Control Rbac Cloudflare
What Is Role Based Access Control Rbac Cloudflare
Github Umair Khanzada Role Based Access Control Role Based Authorization Role Based Access Control In React Js
 Attribute Based Access Control Beyond Roles Axiomatics
Attribute Based Access Control Beyond Roles Axiomatics
Scheme Of Role Based Access Control Rbac Model Download Scientific Diagram
No comments:
Post a Comment
Note: only a member of this blog may post a comment.