The Zero Trust model of information security basically kicks to the curb the old castle-and-moat mentality that had organizations focused on defending their perimeters while assuming everything. Zero Trust is a strategic initiative that helps prevent successful data breaches by eliminating the concept of trust from an organizations network architecture.
 Five Best Practices For Zero Trust Security Centrify
Five Best Practices For Zero Trust Security Centrify
The way businesses operate has changed.

What is zero trust security. Zero Trust architecture uses strict security protocols to grant access while keeping authenticated users continually protected from malware data exfiltration and other cybersecurity attacks. Zero trust is a network security philosophy that states no one inside or outside the network should be trusted unless their identification has been thoroughly checked. Zero Trust is a data security approach that focuses on not trusting any users inside or outside of an organization in order to protect important resources.
In short a Zero Trust approach trusts no one. A zero trust architecture ZTA is an enterprises cyber security plan that utilizes zero trust concepts and encompasses component relationships workflow planning and access policies. With this methodology networks and security systems start from a posture of denying trust by default and work to incrementally open access to users while continuously evaluating risk.
This article teaches everything you need to know about the Zero Trust security model. Zero Trust is a security strategy that meets the complex safety needs of a modern work environment. Regardless of where the request originates or what resource it accesses Zero Trust teaches us to never trust always verify.
Its imperative to understand what Zero Trust is as well as what Zero Trust isnt. Prior to this notion of zero trust most security teams relied on a trust but verify approach that emphasized a strong defensive perimeterThis model assumes anything within the network perimeter including an organizations users resources and applications is trustworthy so security teams granted access and privileges to those users and resources by default. Zero Trust is a security concept that requires all users even those inside the organizations enterprise network to be authenticated authorized and continuously validating security configuration and posture before being granted or keeping access to applications and data.
Emails and files are encrypted before they leave the senders computer and only decrypted when they reach the destination keeping data protected wherever it. Zero Trust is an advanced security approach where all users inside and outside an organizations network must be authorized authenticated and validated continuously of their security posture and configuration before they are granted access to the network data and applications. Instead of assuming everything behind the corporate firewall is safe the Zero Trust model assumes breach and verifies each request as though it originates from an open network.
Zero Trust Security and Virtru. Virtrus data-centric encryption contributes to Zero Trust network security. Zero Trust is a shift of network defenses toward a more comprehensive IT security model that allows organizations to restrict access controls to networks applications and environment without sacrificing performance and user experience.
It is designed to enable least privilege access narrowly limiting the application or resource a user or device can connect to. What is zero trust security. This security setup is ideal for protecting a company that relies on cloud computing remote workforces and distributed systems.
Zero Trust is a network security model designed to handle the challenges of modern IT environments. A zero trust network is one in which no person device or network enjoys inherent trust. Zero-trust security is an IT security model that limits who can access applications and dataincluding an organizations employees.
Zero Trust has become one of cybersecuritys latest buzzwords. Data is stored beyond corporate walls and limitless connections have given rise to remote working. All trust which allows access to information must.
Zero Trust is a security concept centered around the belief that organizations should never trust users or devices attempting to access data and systems within the network until their legitimacy has been verified. Zero trust operates on the assumption that threats both outside and inside the network are an omnipresent factor.
 What Is Zero Trust And Why Is It So Important
What Is Zero Trust And Why Is It So Important
 Arsitektur Keamanan Zero Trust Security Pt Netsolution
Arsitektur Keamanan Zero Trust Security Pt Netsolution
 Microsoft Zero Trust Security Sereno Cloud Solution
Microsoft Zero Trust Security Sereno Cloud Solution
 Zero Trust Security Concepts And Microsoft 365 Infused Innovations
Zero Trust Security Concepts And Microsoft 365 Infused Innovations
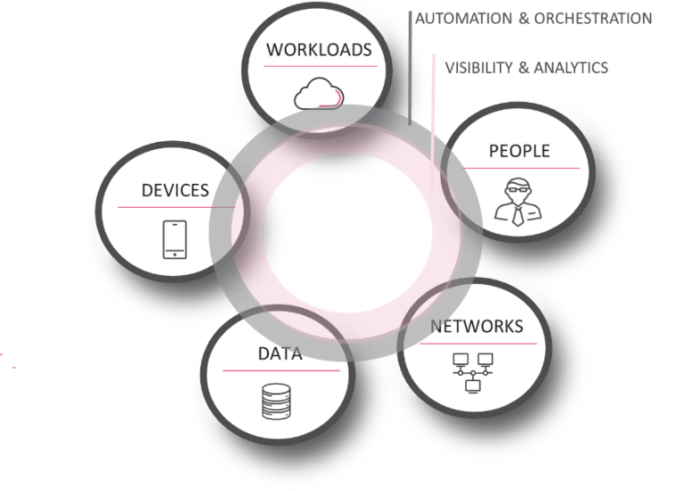 What Is Zero Trust Security And Why Should You Care Check Point Software
What Is Zero Trust Security And Why Should You Care Check Point Software
 What Is Zero Trust A Comprehensive Security Model Varonis
What Is Zero Trust A Comprehensive Security Model Varonis
 Zero Trust Security What S A Zero Trust Network Cloudflare
Zero Trust Security What S A Zero Trust Network Cloudflare
 Absolute Zero Trust Security Check Point Software
Absolute Zero Trust Security Check Point Software
![]() Zero Trust Security Complete Guide And How To Implement It
Zero Trust Security Complete Guide And How To Implement It
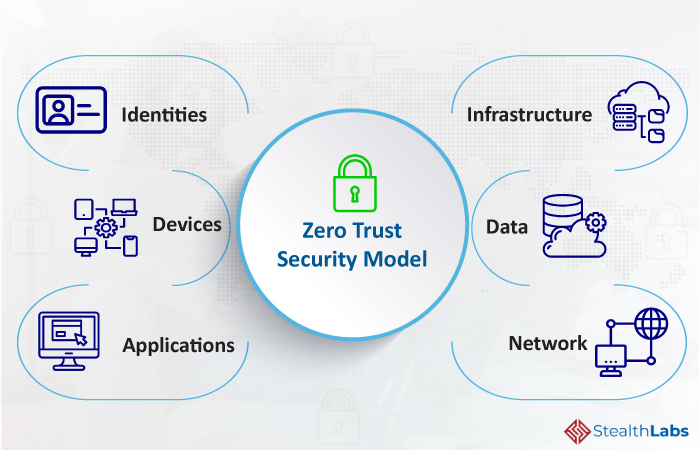 How Businesses Can Implement Zero Trust Security
How Businesses Can Implement Zero Trust Security
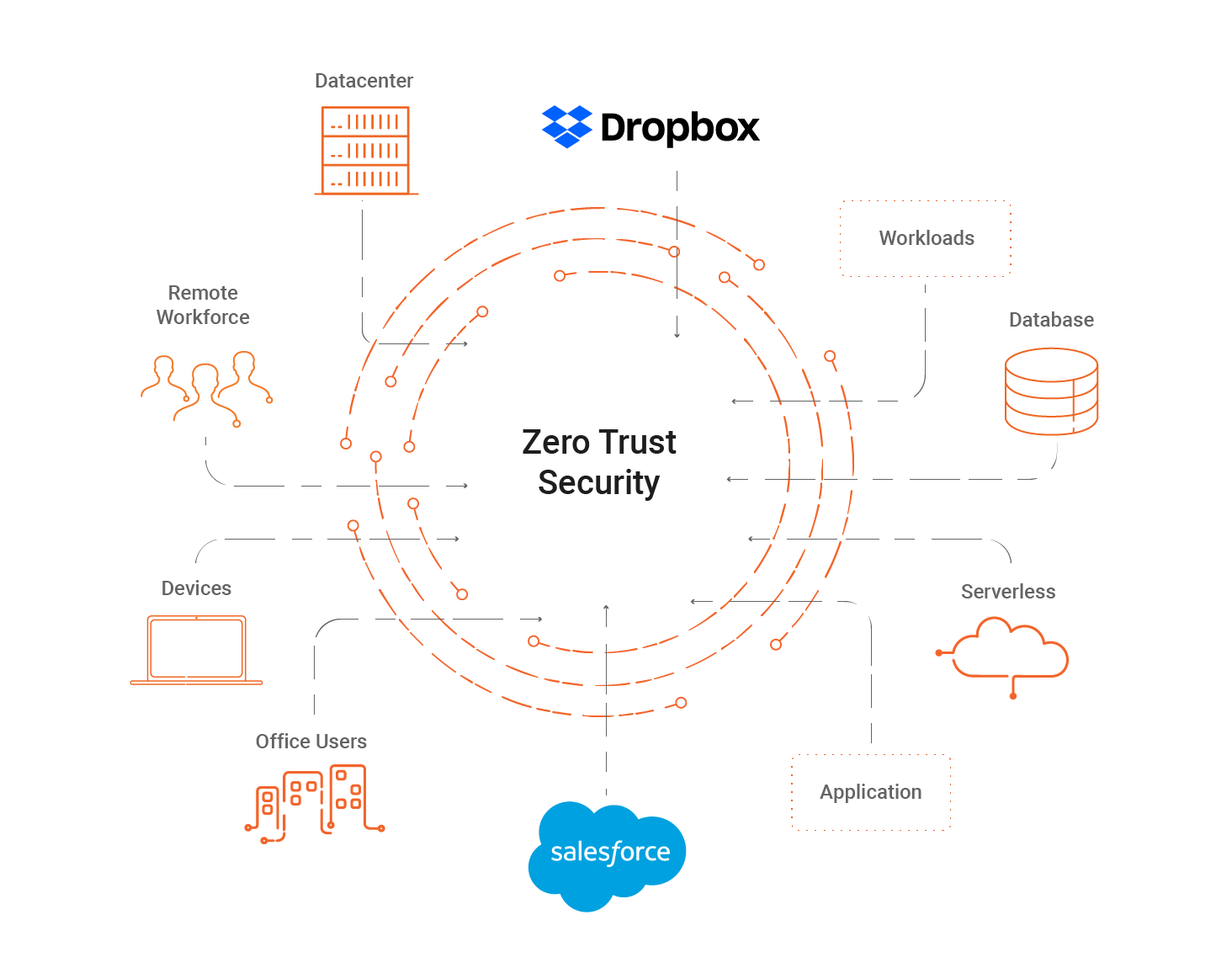
 Cloud Security Zero Trust Master Concept
Cloud Security Zero Trust Master Concept


No comments:
Post a Comment
Note: only a member of this blog may post a comment.