In short a Zero Trust approach trusts no one. Microsoft deployed Zero Trust to secure corporate and customer data.
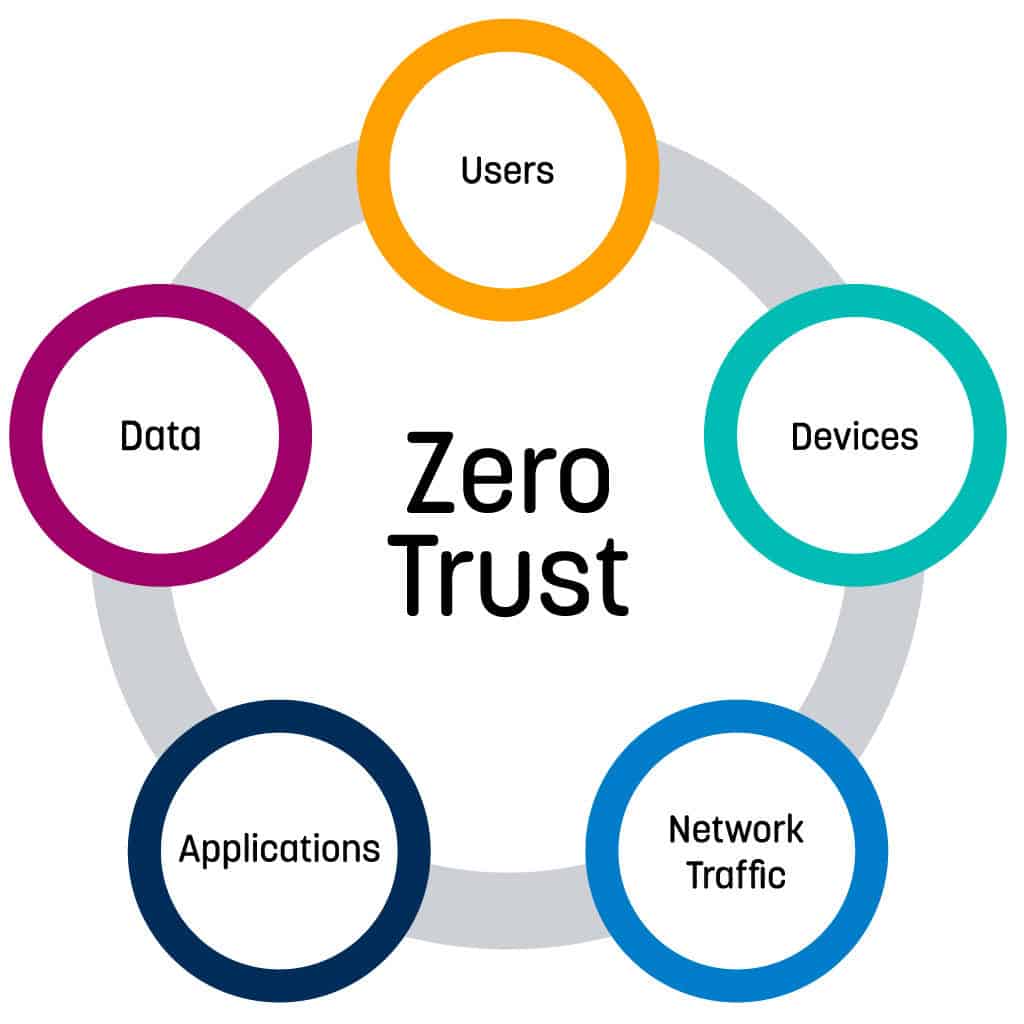 Embracing A Zero Trust Security Model Logrhythm
Embracing A Zero Trust Security Model Logrhythm
The traditional approach automatically trusted users and endpoints within the organizations perimeters putting the organization at risk from malicious internal actors and allowing unauthorized users wide-reaching access.
Zero trust security. Zero-trust security is an IT security model that limits who can access applications and dataincluding an organizations employees. Zero trust security is a concept thats been around for several years but it may finally be starting to gain traction as a technology product. Adoption of zero trust can help address common security challenges in the workforce such as phishing malware credential theft remote access and device security BYOD.
Zero Trust is a shift of network defenses toward a more comprehensive IT security model that allows organizations to restrict access controls to networks applications and environment without sacrificing performance and user experience. Zero Trust has become one of cybersecuritys latest buzzwords. Zero trust is a strategic approach to security that centers on the concept of eliminating trust from an organizations network architecture.
Increase the difficulty of compromising your cloud footprint. Ad Enable zero trust with RSA to modernize your security accelerate digital transformation. Zero trust is a network security philosophy that states no one inside or outside the network should be trusted unless their identification has been thoroughly checked.
Google zero trust tools can protect your workloads on any public cloud or on-premises so you dont need to move your applications to improve their security. The implementation centered on strong user identity device health verification validation of application health and secure least-privilege access to corporate resources and services. Its imperative to understand what Zero Trust is as well as what Zero Trust isnt.
What is zero trust security. Ad Enable zero trust with RSA to modernize your security accelerate digital transformation. Trust is neither binary nor permanent.
Zero Trust is a strategic initiative that helps prevent successful data breaches by eliminating the concept of trust from an organizations network architecture. Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything. In the Zero Trust model there are three key objectives when it comes to securing your networks.
Users their devices and the applications they access. The US National Institute of Standards and Technology NIST in its current draft of standards for zero trust architecture defines zero trust basically as Zero trust. This is done by securing the three primary factors that make up the workforce.
The zero trust security model also zero trust architecture zero trust network architecture ZTA ZTNA sometimes known as perimeterless security describes an approach to the design and implementation of IT systemsThe main concept behind zero trust is that devices should not be trusted by default even if they are connected to a managed corporate network such as the corporate LAN. Benefits of zero trust Lower friction. Zero trust operates on the assumption that threats both outside and inside the network are an omnipresent factor.
We can no longer assume that internal entities are trustworthy that they can be directly managed to reduce security risk or that checking them one time is enough. Zero Trust architecture uses strict security protocols to grant access while keeping authenticated users continually protected from malware data exfiltration and. Minimize the extent of the damage and how fast it spreads.
Zero Trust is a significant departure from traditional network security which followed the trust but verify method. With this methodology networks and security systems start from a posture of denying trust by default and work to incrementally open access to users while continuously evaluating risk. Zero Trust is a data security approach that focuses on not trusting any users inside or outside of an organization in order to protect important resources.
Be ready to handle attacks before they happen.
 Cloud Security Zero Trust Master Concept
Cloud Security Zero Trust Master Concept
 Zero Trust Security What S A Zero Trust Network Cloudflare
Zero Trust Security What S A Zero Trust Network Cloudflare
![]() Zero Trust Security Complete Guide And How To Implement It
Zero Trust Security Complete Guide And How To Implement It
 How To Implement Zero Trust Security Globaldots
How To Implement Zero Trust Security Globaldots
 Pulse Connect Ushers Persol Towards Zero Trust Architecture Frontier Enterprise
Pulse Connect Ushers Persol Towards Zero Trust Architecture Frontier Enterprise
 Arsitektur Keamanan Zero Trust Security Pt Netsolution
Arsitektur Keamanan Zero Trust Security Pt Netsolution
 What Is Zero Trust A Comprehensive Security Model Varonis
What Is Zero Trust A Comprehensive Security Model Varonis
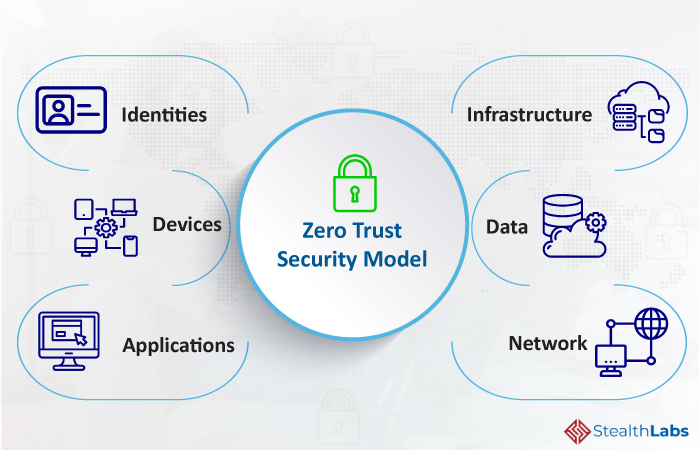 How Businesses Can Implement Zero Trust Security
How Businesses Can Implement Zero Trust Security
 Zero Trust Extended Security Model Pt Netsolution
Zero Trust Extended Security Model Pt Netsolution
 Absolute Zero Trust Security Check Point Software
Absolute Zero Trust Security Check Point Software
 What Is Zero Trust And Why Is It So Important
What Is Zero Trust And Why Is It So Important
 Microsoft Zero Trust Security Sereno Cloud Solution
Microsoft Zero Trust Security Sereno Cloud Solution
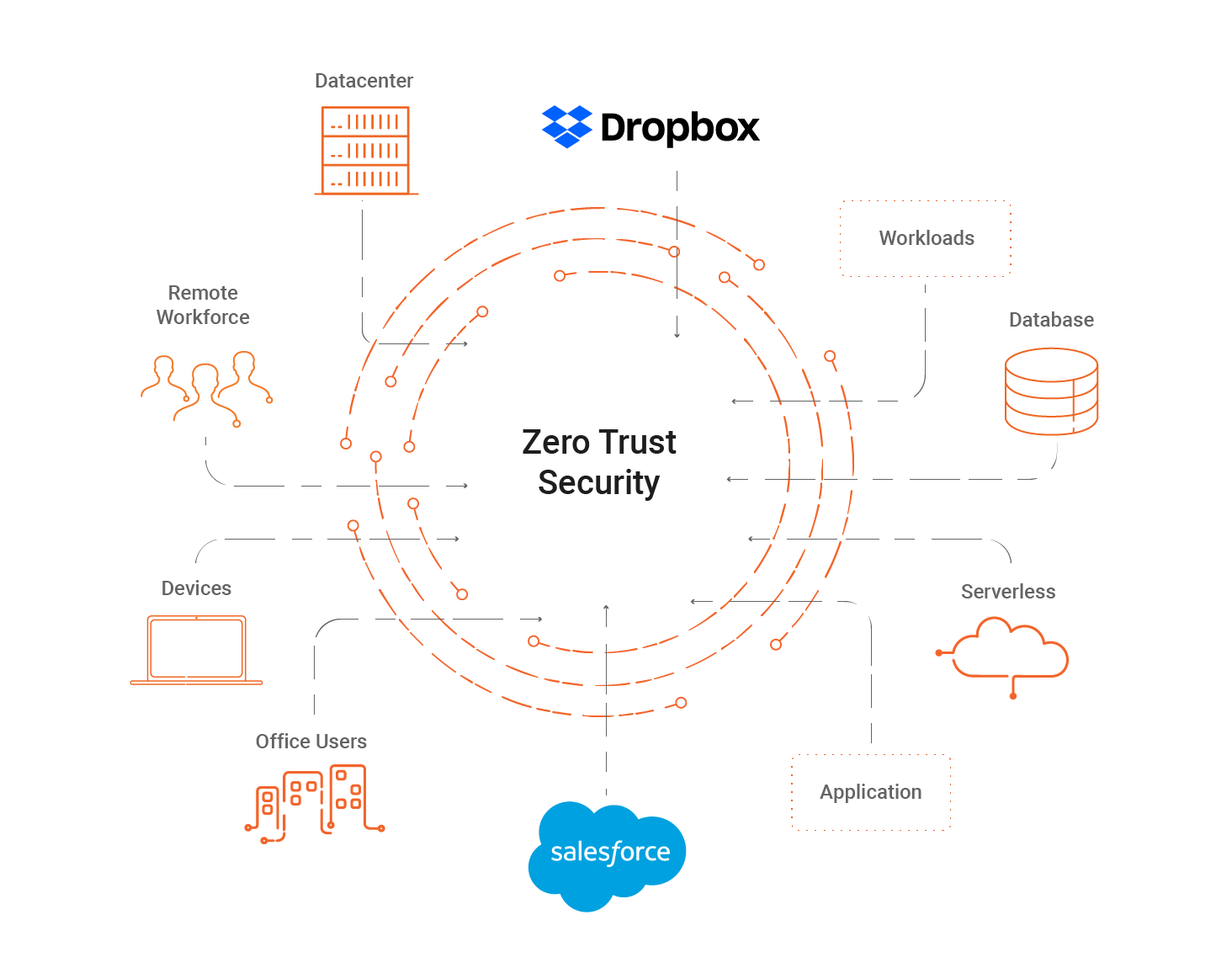

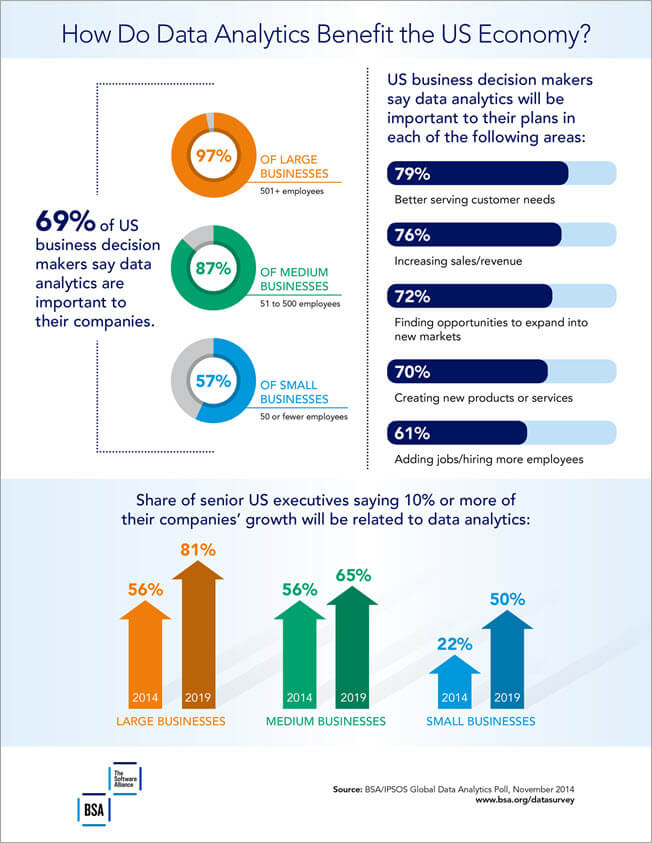
No comments:
Post a Comment
Note: only a member of this blog may post a comment.